The Security Benefits of Infrastructure as Code
We have developed and delivered new ways to deliver infrastructure quickly and without these misconfigurations. Prevention is the only cure; we’ll talk about how you can implement this today.
We’re over two decades into the cloud computing journey, and we’re still learning what works and doesn’t. A common issue we see across the board during our cloud security assessments is security misconfiguration. It’s not hard to understand why this happens. Each AWS service has multiple configuration settings that must be managed. It is common for resources to be deployed manually or through automation that is not validated. This leads to a huge proliferation of misconfigurations, a lot of which are high-risk. According to IBM’s Cost of a Data Breach Report, 82% of breaches are related to data in the cloud. With every client we work with, we see this happening, from large to small. As you scale your cloud environment, these misconfigurations pile up, making remediation almost impossible. We have developed and delivered new ways to deliver infrastructure quickly and without these misconfigurations. Prevention is the only cure; we’ll talk about how you can implement this today.
What is Infrastructure as Code?
It's essential to understand what Infrastructure as Code (IaC) is, before we delve into the security benefits. IaC is the process of managing and provisioning infrastructure (computing, data storage, pizza, etc.) through configuration and definition files rather than clicking through the console or writing scripts tying together the CLI. It allows developers to automate processes, reduce manual errors, and ensure a consistent environment across various stages of the software development life cycle.
Terraform, an open-source IaC tool created by HashiCorp, stands out for its simplicity, ease of use, and compatibility with numerous cloud service providers. It allows developers to write, plan, and create reproducible infrastructure using a high-level configuration language, making it an excellent tool for managing complex or large-scale infrastructures. It also manages the state to ensure that drift can be corrected. This makes Terraform unique from other tools that don’t manage the state and can cause a mismatch between code and the environment.
Integrating Security into IaC
Implementing security measures directly into your IaC process is a simple way to enhance your security posture while keeping developer friction to a minimum. This integrated approach ensures that security checks and policies are incorporated into your infrastructure from the start rather than being retrofitted later on.
With Terraform, you can integrate various security tools, such as static code analyzers and linters, into your infrastructure management process. These tools can detect potential security issues before they become a threat, ensure the use of best practices, and streamline the process of managing security policies. With clients, we’ve implemented IaC security programs and have seen a dramatic decrease in misconfigurations in their cloud environment. We often review their CSPM findings to ensure they have no coverage gaps in their IaC security tooling and see almost no misconfiguration-related findings. It is simply not possible to remediate cloud security issues at scale. We must move to a preventative model.
Here are some of the key security benefits of using IaC tooling like Terraform:
Consistent Environments
With IaC, you can create consistent, reproducible environments across different stages of the software development life cycle. This consistency reduces the potential for security vulnerabilities that may arise from configuration drift or inconsistencies between environments.
Immutable Infrastructure
Terraform promotes the concept of immutable infrastructure, where components are replaced rather than changed. Think cattle, not pets. We move away from long-running infrastructure towards easily replaceable resources. This approach ensures that any changes are traceable and reduces the risk of configuration drift, a significant source of security vulnerabilities.
Version Control and Auditability
When using IaC, your infrastructure's configuration is stored as code in a version control system. This approach provides an audit trail for all changes made to the infrastructure, making it easier to identify and remediate any security issues. This also gives you a very strong integration point with your security tooling.
Early Detection of Security Vulnerabilities
By integrating security tools into your Terraform workflow, you can identify potential security vulnerabilities before your infrastructure is deployed. For example, static code analyzers can detect insecure coding practices, while security-focused testing tools can identify potential vulnerabilities in your infrastructure.
Automated Compliance Checks
Terraform can be integrated with tools that automate compliance checks, ensuring your infrastructure adheres to regulatory requirements and industry best practices. This automation helps reduce the risk of non-compliance and the potential for security breaches.
Specifications
One of the benefits of IaC tooling is that it is specification-driven. Often, in the application security space, we integrate static analysis tools, and we see a spike in false positives due to the tools misunderstanding the relationship of different components. IaC doesn’t suffer from this issue as much. Each resource in Terraform has a specific configuration that has certain attributes. Writing tooling to enforce values here is more straightforward as we generally know the values, and they are of a basic type, e.g., boolean, text, etc. There are fewer levels of abstraction, but there are edge cases when using modules where some values aren’t easily referenced. Terraform does have a unique challenge for security integration after unknowns. The reason behind them is explored in more detail in this blog. We’ll write more in the future about the security challenges of them and how to work around them.
Security tooling
Now, are you wondering what the available tools are to integrate with your IaC pipeline? Well, the great news is there are many, and many are free.
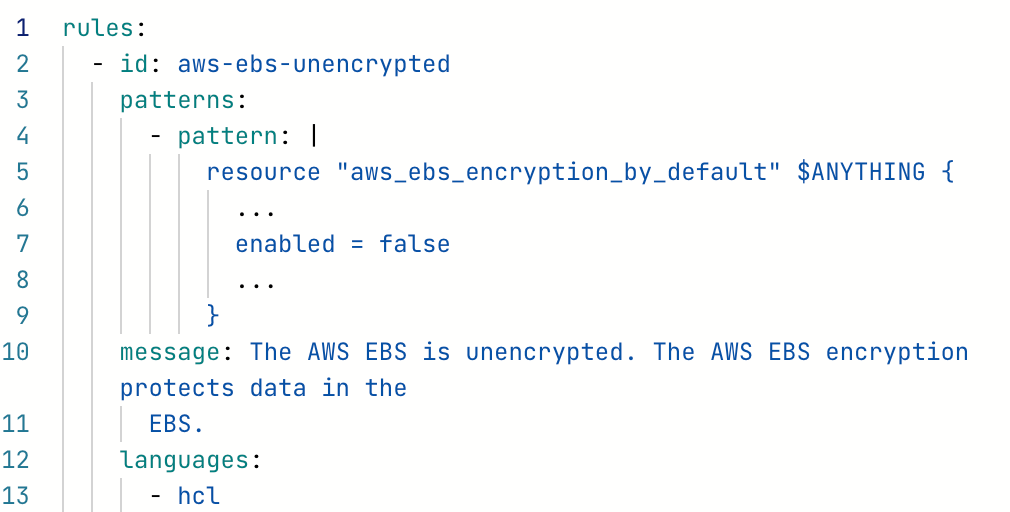
A static analysis tool that we often use, Semgrep supports Terraform. We like Semgrep because it’s free, easy to integrate, and runs quickly. There is a paid version, but you don’t need that to get started. Currently, there are 61 rules in Semgrep for Terraform. One of the main reasons we like Semgrep is its ease of use and writing of new rules.
By utilizing pattern matching and some helper functions in Semgrep, you can create rules quickly for custom use cases. The following shows how to detect unencrypted EBS volumes in six lines of code.
There are a few Terraform-specific tools as well.
Tfsec, created by Aqua Security, has a rich ruleset and is fast to run.
A non-Terraform-specific tool is Chechov, which is a tool meant for validating infrastructure as code, including Terraform, Helm charts, Docker files, etc.
Another Terraform-specific tool is Terrascan by Tenable.
All of these tools are great and worth integrating into your pipeline to start validating your IaC code. In future blog posts, we’ll cover how to integrate IaC security tools into your pipeline and how to start building your policy as a code program. If you'd like a brief overview of the results of those tools check out this post.
Utilizing Terraform to deploy infrastructure offers many benefits to creating a more secure environment. Terraform increases the ways to improve the security of your cloud environment at scale without scaling up your cloud security team. Integrating security into your IaC pipeline is straightforward and gives actionable results. Reach out today if you’d like help starting your IaC security program and see your cloud findings go to zero.




